The Security Tree object class allows Admins to control access to object records based on a hierarchical structure, similar to a tree. Admins can assign users and records to nodes within a security tree to provide record-level access. User application role access can cascade down through a hierarchy while visibility to object records can roll up through a hierarchy.
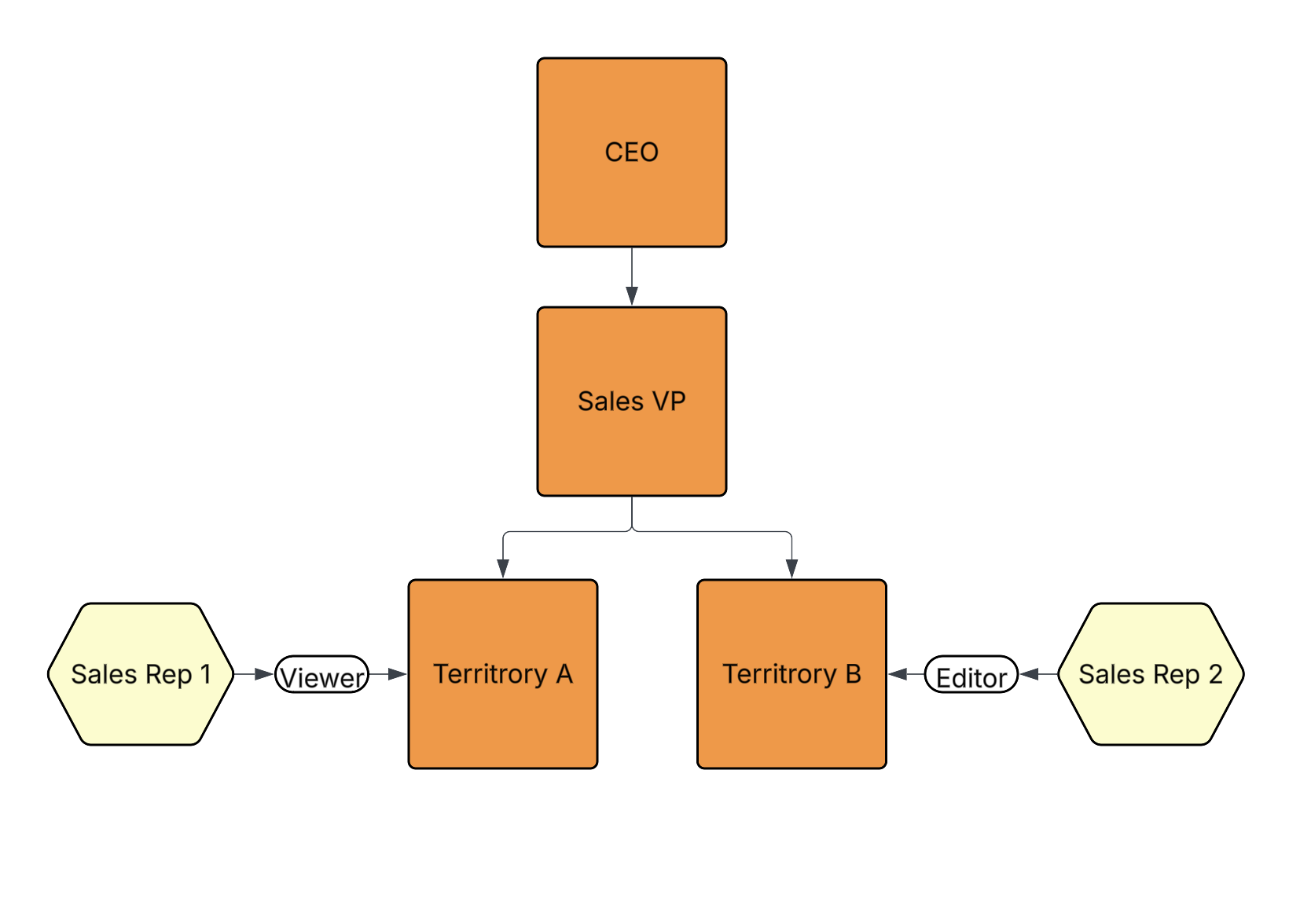
For example, in the diagram below, VernBio’s sales team is organized by a CEO, Sales VP, Territory A, and Territory B. Each point in the hierarchy is considered a security tree node. In this structure, Sales VP is a child node of CEO, and Territory A and Territory B are child nodes of Sales VP.
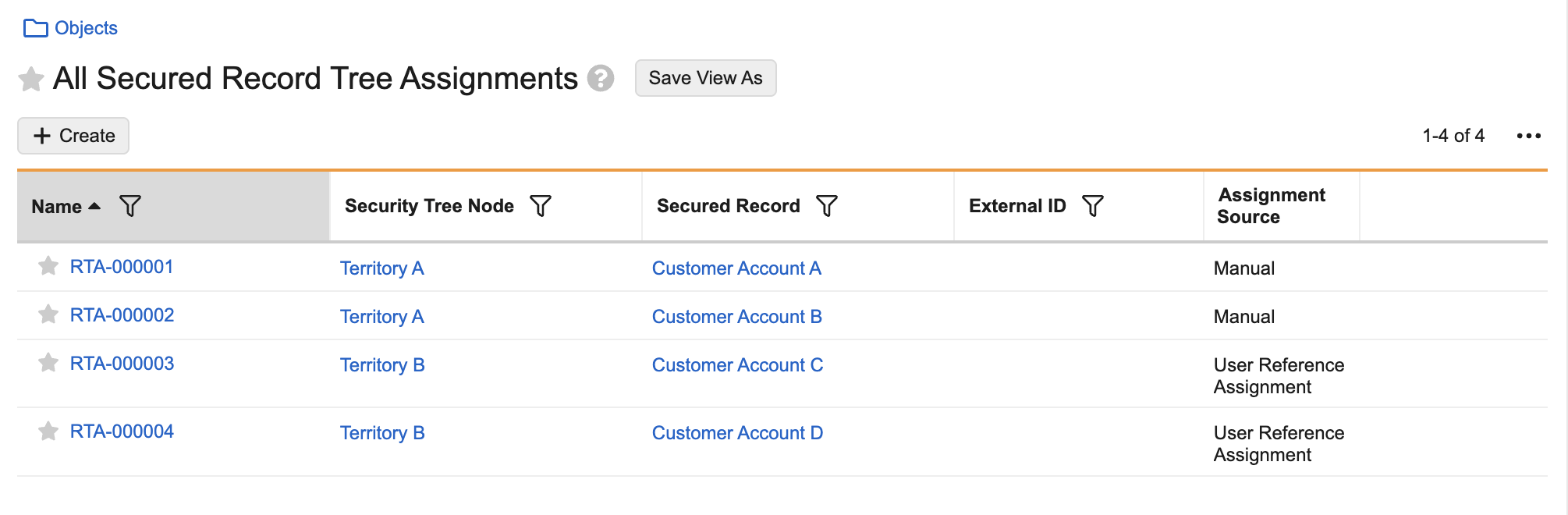
Sales Reps (users) are assigned to the Territory A and Territory B nodes with application roles.
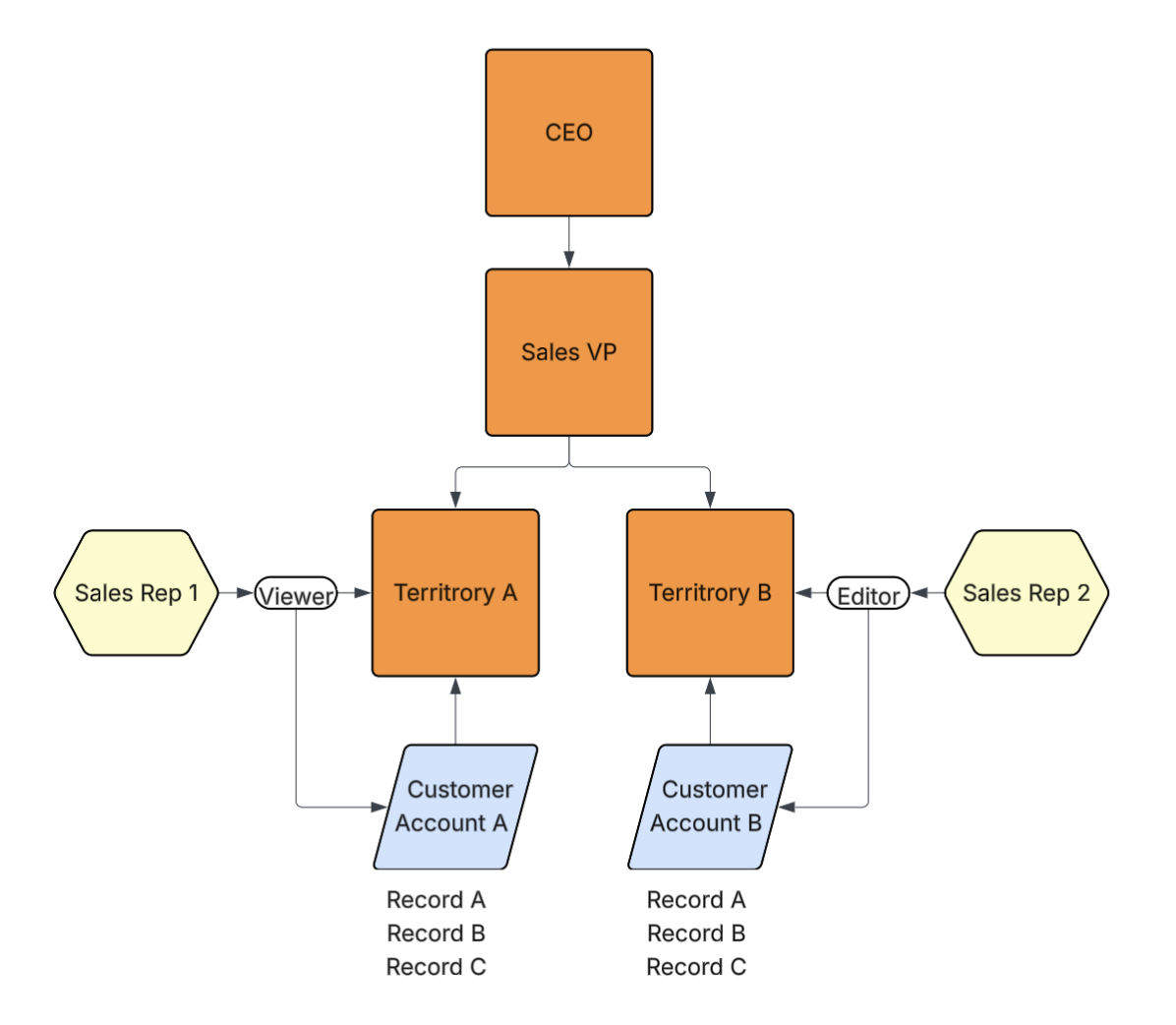
Customer accounts (object records) are also assigned to the Territory A and Territory B nodes. Once a user is assigned into a security tree via a node, they gain the specified application role access to records assigned to the same node, or any child nodes. In the diagram below, Sales Rep 1 is granted Viewer access to customer accounts assigned to Territory A, and Sales Rep 2 is granted Editor access for customer accounts assigned to Territory B.
Users assigned to the CEO node receive similar access to customer accounts assigned to the CEO node in addition to customer accounts assigned to the Sales VP, Territory A, and Territory B nodes. The same behavior applies to the Sales VP node, but users assigned to this node will not have access to customer accounts assigned to the CEO node.
You can use Security Tree-class objects in conjunction with existing security controls on an object or object records, such as custom sharing rules, matching sharing rules, manual assignments, and Atomic Security.
Configuring a Security Tree
When creating a custom object, select Security Tree as the object class. There are two (2) additional fields specific to only the Security Tree object class:
- User Tree Assignment Object Name: This name is assigned to the automatically generated object with the User Tree Assignment object class applied. Once created, you cannot change this name. However, you can modify the label and plural label. This field is required.
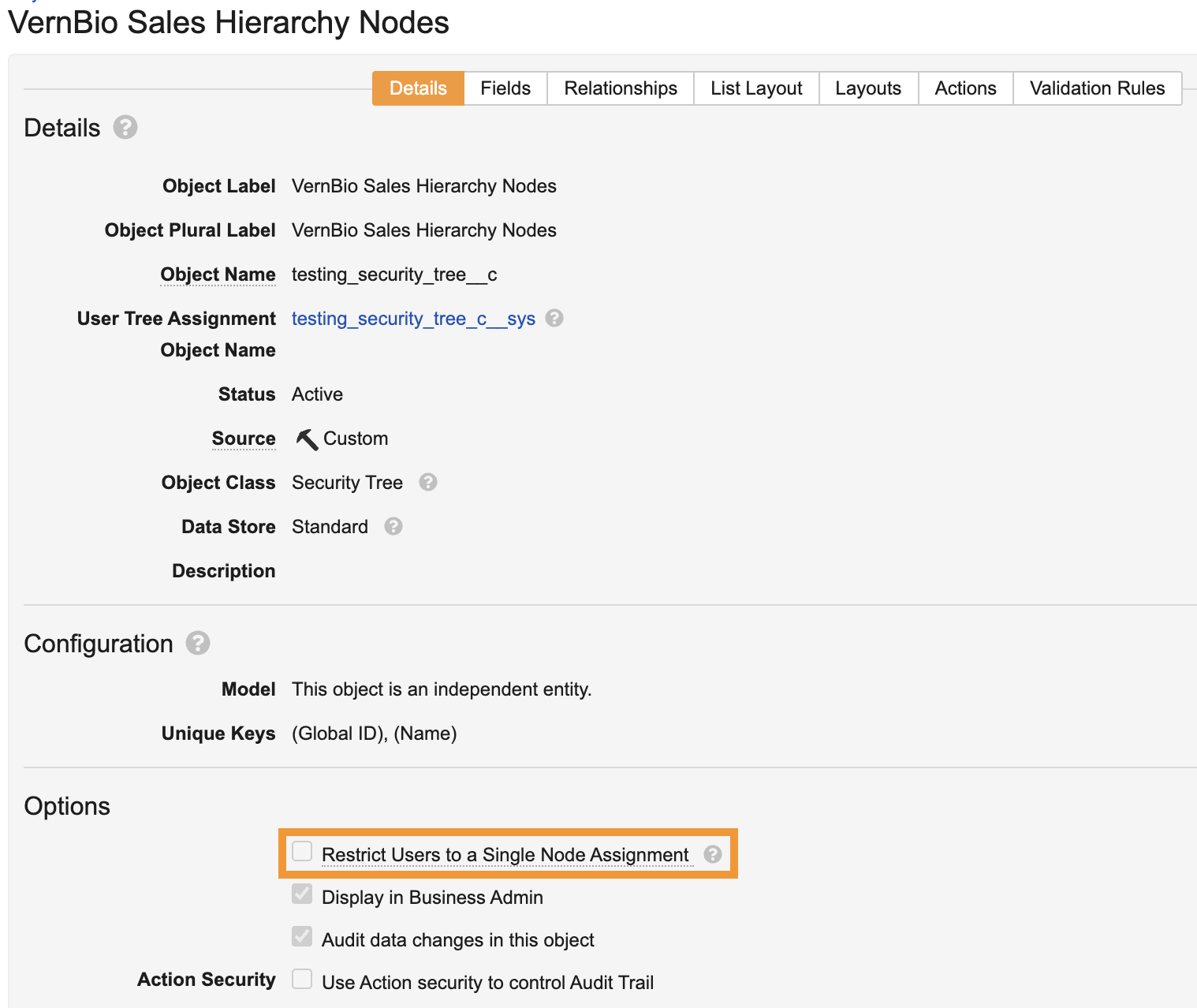
- Restrict Users to a Single Node Assignment: Allows you to restrict users to one (1) node within the security tree. Enabling this field allows you to leverage the User Reference Assignment field to automatically assign object records to the Security Tree. This field is optional.
Once saved, Vault creates a raw object with the User Tree Assignment object class applied to capture application role assignments for users within the Security Tree.
Once the Security Tree-class object is created, you can secure additional objects and their records within your security tree. When you create or edit a custom object, the Details tab contains a Security Tree Object field that displays all Security Tree-class objects in your Vault. Select a Security Tree and then enter a Tree Assignment Object Name.
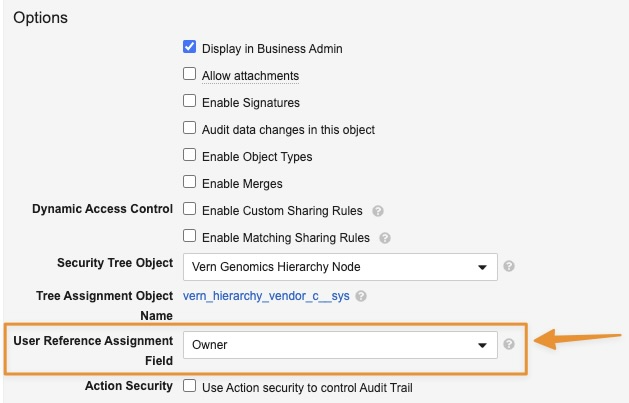
Once you save the secured object, Vault creates the raw object with the Secured Record Tree Assignment object class applied and the name you entered. This object allows you to provide users record-level access via the Security Tree. In addition, if Restrict Users to a Single Node Assignment is enabled on the selected security tree, the User Reference Assignment drop-down becomes available in the secured object’s Details section.
Objects with the User Tree Assignment or Secured Record Tree Assignment class are system-managed and cannot be created in Vault.
Note: The Security Tree Object field may not be available on certain standard objects based on application preferences.
Secured Record Lifecycle
When a lifecycle is not configured on a secured object, only the following standard application role assignments from the security tree are evaluated at runtime: Owner, Editor, Viewer. Once the lifecycle is configured, custom application role assignments within the object’s lifecycle are applied to the security tree.
Users gain implicit Read permission to records assigned to their node or child nodes. If a user is assigned a custom application role with no permissions in the secured object’s lifecycle, the user only receives Read permission to any records assigned to their node or child nodes. If the custom application role is not configured on the secured object, any permissions on the role are not applied in the security tree as the role is not considered valid.
Vault considers an application role assignment in a security tree valid only if it is standard (Owner, Editor, or Viewer) or a custom application role enabled within the secured object’s lifecycle. When assigning users to custom application roles, it is recommended to grant these roles Read permission within their corresponding secured object’s lifecycle. This action reflects the implicit Read permission granted through the security tree.
Note: User Tree Assignment-class objects created after 25R2.3 will not contain the criteria VQL used to constrain these records to the Owner, Editor, Viewer roles. You must manually remove the VQL constraint on User Tree Assignment-class objects created prior to 25R2.3.
How to Create Security Tree Nodes
To create a security tree node:
- Create a record on the Security Tree-class object.
- Enter a Name for the node.
- Optional: Select a Parent Node. Only one node on the security tree is allowed to not have a parent node. This node is considered the root node.
- Click Save.
The security tree node is now created. Repeat this process to add additional nodes to the security tree.
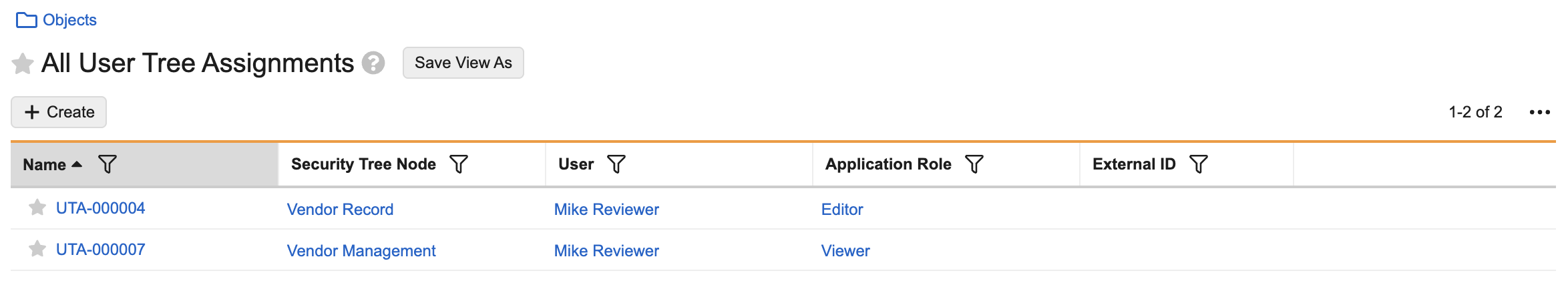
Users gain direct application role access to object records assigned to their node and its child nodes. For example, in the image below, Mike Viewer has Viewer access to any records assigned to the Vendor Management node as well as its child node Vendor Record. Mike Reviewer also has Editor access to the Vendor Record node, providing him Editor and Viewer access to records on this node.
Deleting a Security Tree
Deleting a Security Tree-class object deletes any corresponding objects with the User Tree Assignment or Secured Record Tree Assignment object class applied. If records exist on the User Tree Assignment-class or Secured Record Tree Assignment-class object, you must delete those records before deleting the security tree. This same behavior applies to removing a security tree from a secured object.
Deleting a Security Tree Assignment
Deleting a user from a node removes the user’s access to any records on the node and its child nodes. Deleting a record from a node only removes the user’s access and visibility to the record on that node.
However, deleting a user or record from a node does not impact additional security configured on the record. For example, if Mike Reviewer has access to Record 1 on the Vendor Record node through custom sharing rules, the user does not lose custom sharing rule access if the record is deleted from the node.
Static Assignments
A static assignment refers to manually assigning a user to a Security Tree Node through the User Tree Assignment-class object or assigning a record to a node through the Secured Record Tree Assignment-class object. Records created on objects with these classes applied store the static assignments within the Security Tree.
Note: If an application role used in a security tree is made inactive, assignment of the role will cease and it will no longer be available for selection in User Tree Assignment-class records.
User Tree Assignment
Objects with a User Tree Assignment object class allow you to assign a user to a node in a security tree with an assigned application role. To use this object to assign a user to a security tree node:
- Create a record on the User Tree Assignment-class object.
- Select the status as Active or Inactive.
- Optional: Select a Security Tree Node. Although this field is optional, you must select a Security Tree Node to assign the user to it.
- Select a User to assign to the Security Tree Node selected above.
- Select the user’s Application Role.
- Optional: Enter an External ID.
- Click Save.
The user is now assigned to the Security Tree Node. You can assign the user to additional nodes if Restrict Users to a Single Node Assignment is not enabled.
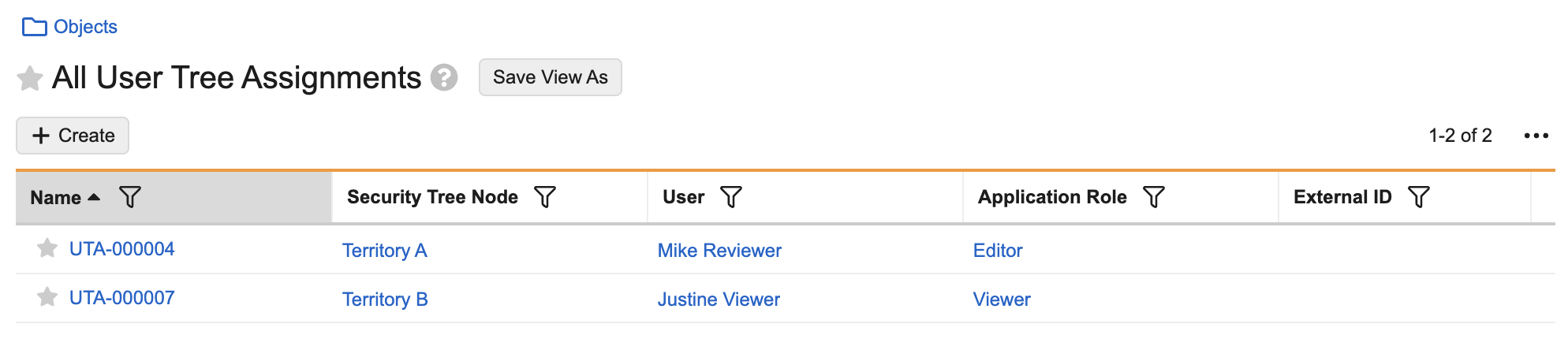
In the image below, Mike Reviewer is assigned to the Territory A node with Editor access to any records assigned to the node and its child nodes. Justine Viewer is assigned to the Territory B node with Viewer access to any records assigned to the node and its child nodes.
Secured Record Tree Assignment
Objects with a Secured Record Tree Assignment object class allow you to assign object records to a Security Tree. Objects with this class are available only if you secured an object by selecting a security tree on the object’s Details tab. To use this object to assign an object record to a Security Tree Node:
- Create a record on the secured object.
- Create a record on the Secured Record Tree Assignment-class object.
- Select the status as Active or Inactive.
- Optional: Select a Security Tree Node. Although this field is optional, you must select a Security Tree Node to assign the record to it.
- Optional: Select a Secured Record. This field populates all records created on the secured object.
- Optional: Select an External ID.
- Click Save.
The object record is now assigned to the Security Tree Node. Any users assigned to this node will gain access to the record based on their assigned application role.
In the image below, object records Customer Account A and Customer Account B are assigned to the Territory A node and Customer Account C and Customer Account B are assigned to the Territory B node.
Single User Tree Assignment
A single user assignment refers to restricting a user to only one node in the Security Tree. You must enable Restrict Users to a Single Node Assignment on the Security Tree-class object to use this functionality. Once enabled, you can use the User Reference Assignment field when securing an object by a Security Tree.
If the User Reference Assignment field on a secured object contains a value, you cannot clear this checkbox.
This setting is available only if no static assignments exist for users on the Security Tree.
User Reference Assignment
A user reference assignment refers to automatically assigning records to a Security Tree based on an existing static user assignment. When creating a secured object, you can select any user reference field on the secured object from the User Reference Assignment drop-down. Then, when you create a record on the secured object, you can select a user from the user reference field. Once the record is saved, Vault automatically assigns the object record to the selected user’s node.
If the selected user is not assigned to a node, Vault creates the record but the assignment does not occur. In this case, the record is not visible to the user in Vault.
User reference assignment applies to future records and not existing ones. In addition, previous record assignments created through user reference assignment are not impacted. However, it is recommended to remove users from these assignments so that previous application role access is removed on records prior to selecting a new user reference assignment field.
Limits
The following limits apply to objects with a Security Tree object class:
- Up to one node without a parent, or root node, is allowed per Security Tree.
- Up to ten levels of parent node-child node relationship allowed.
- Up to 50,000 nodes are allowed per Security Tree.
- Up to 70 objects can be secured by a Security Tree.
- You can assign a single user to 100 nodes in a Security Tree.
- You can assign a single object record to 200 nodes in a Security Tree.
- You cannot select the Security Tree object class if Replicate sharing settings from parent object is enabled on the object.
- If a parent object is secured by a Security Tree, you cannot modify Security Tree configurations on the child object if Replicate sharing settings from parent object is enabled.
- Object types are not supported.
- Only standard data store is supported.
- You cannot create custom fields or enable object lifecycles on User Tree Assignment-class objects and Secured Record Tree Assignment-class objects.